A major, multipronged Kiwi organisation came to us in a bit of a panic: its trusted, well-known brand was being used in phishing campaigns across the world. It knew the domain was being misused and its brand damaged, but it was powerless to do anything about it. The organisation also couldn’t tell how widespread the issue was or what the fallout might be.
Senior leaders managed to provide a sample of the phishing emails from customers, which made it clear what SMX needed to do next – implement DMARC to quantify the issue and immediately fix it.
That’s because DMARC protects against spoofing and impersonation by publishing information on how an email from a domain should be handled. This lets inbound mail servers validate domains before allowing them into inboxes. DMARC would also tell us the percentage of mail rejected and give the customer a gauge on the severity of the issue...
DMARC, implemented at pace
The faster SMX moved the more damage we could limit – so we worked quickly, loading domains onto our DMARC platform. Next, we helped our client add the DMARC DNS record and used SPF+DKIM to correct the immediate issues. To save time, and at the customer’s request, we ran in audit/report mode for a few days – a deviation from our best practice systems, but crucial in this case. This let us review and analyse the incoming data to provide a deliverability and risk report to the customer in real time.
While most of the legitimate sending sources were configured correctly, the main newsletter provider was failing part of DMARC. They had DKIM in place and it was passing basic tests, but the domain did align to pass DMARC.
This issue caused redirected messages to fail DMARC, creating an unacceptable risk for the customer, so we moved it to a more aggressive ‘reject’ setting in minutes. In just a few hours we saw this change working at the large mailbox vendors.
Once the newsletter provider reached DKIM alignment we could clearly see hundreds of thousands of spoofed emails being rejected. We knew that the change had significantly reduced the potential brand and reputational damage.
Shown in red below you can see a spoof campaign – emails pretending to be from the customer’s domain – running in near real-time across Gmail, Yahoo and Microsoft - Before implementing DMARC, the customer had no way to see this.
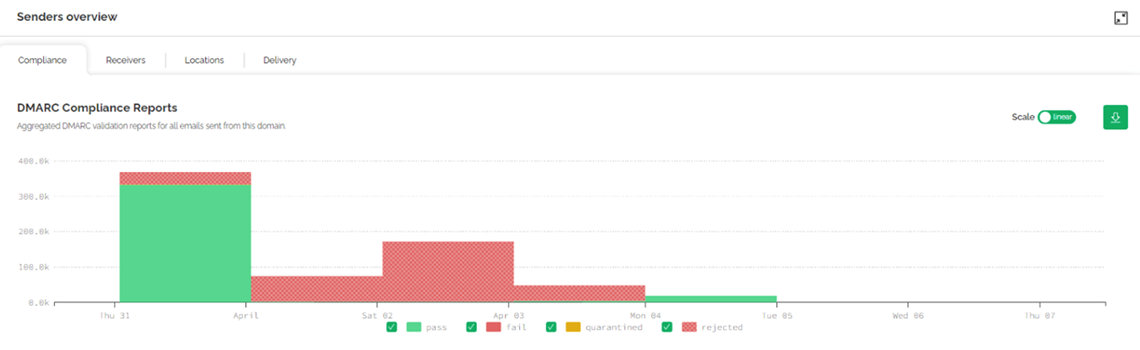
The business benefits were felt immediately, with data-driven answers the ops team could take back to the senior leaders, giving them reassurance the risk had been mitigated.
The results speak for themselves
3.2 million spoof emails stopped in just three months with proper implementation of DMARC, the customer has gotten out in front of the bad actors trying to use its domains in a mail-out. It can quantify the level of spoofed mail being sent to inboxes around the world and was assured that customers were being protected from it. That allowed the leadership team to move on to other important tasks in the business.
The story in numbers:
- 3.2 million spoofed messages stopped over 90 days
- 10.5 million total mail sent by the company’s domains, and likely more
- 31.5% of total mail stopped
- 3,314 messages quarantined
- 99% of stopped mail was spoofed
Learn more about DPS and DMARC Implementation here.

